I’m not a history or politics buff even on the topic of China, but due decades of misinformation on China, especially in the English-speaking world, I find it necessary to speak out with official Chinese sources.
- 2 Posts
- 2 Comments

 1·10 months ago
1·10 months agoI would suggest not posting research papers as news, especially regarding superconductors which was controversial topic last year. I found a Chinese article that references this tweet, which I assume is where you got your post from:
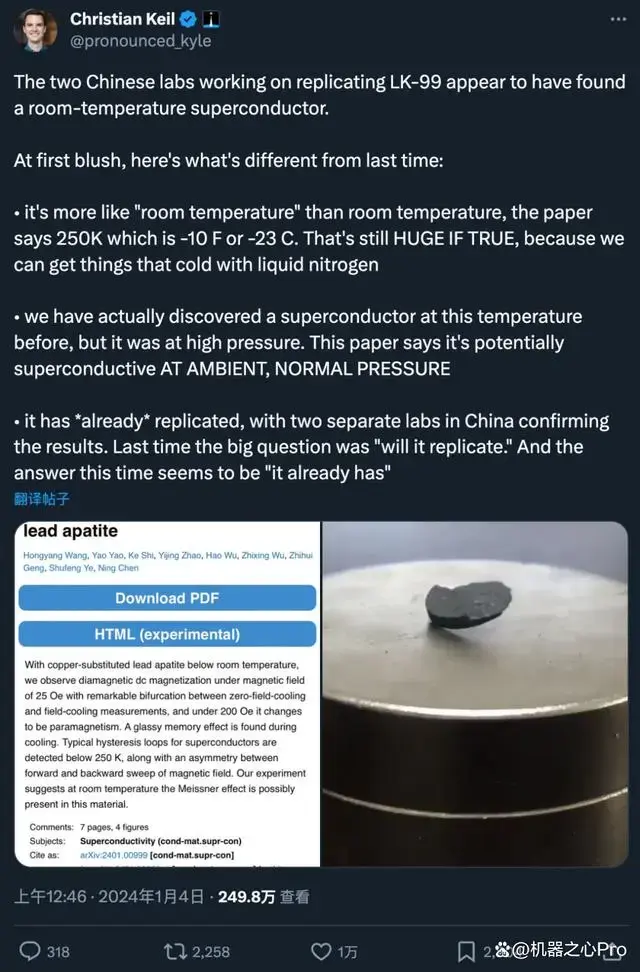
The paper’s title uses “Possible Meissner effect near room temperature”, which does not automatically translate into the sensationalist title “room-temperature superconductor”.
Some of the authors of this paper have responded to questions on Zhihu (something like Chinese Quora) here: https://www.zhihu.com/question/637763289 https://www.zhihu.com/question/637763424
From what I gathered this paper is a milestone on the road to a “near room temperature superconductor”, and there is optimism but more work needs to be done.
The Bloomberg article cited (https://www.bloomberg.com/news/articles/2024-01-09/china-says-cracked-apple-s-airdrop-to-identify-message-sources or https://archive.is/XnvO8) once again doesn’t mention the relevant institute by name, but here’s the Chinese article from Beijing Municipal Bureau of Justice: 2024-01-08 司法鉴定:司法鉴定揭开“隔空投送”匿名传输的神秘面纱 https://sfj.beijing.gov.cn/sfj/sfdt/ywdt82/flfw93/436331732/index.html
This paragraph reveals how they found out the AirDrop sender’s email and phone number:
Basically the sender’s phone number and email addresses were stored as hash values, but the hashes were just partial values. The judicial appraisal institute “北京网神洞鉴” created rainbow tables (precomputed table for caching the outputs of a cryptographic hash function, usually for cracking password hashes) to bruteforce the information.
As Chinese mobile numbers follow certain formats (11 digits, starts with 1, known list of prefixes etc.) it is probably very easy to generate a rainbow table for this. Though the article doesn’t mention if the phone numbers and email had separate hash values so this is just one way to do it.
From Apple’s “AirDrop security” page we can see that this matches up: https://support.apple.com/guide/security/airdrop-security-sec2261183f4/web
This article is about the AirDrop receiver finding out the sender’s information, but doesn’t mention if the reverse is possible. But if we look at the same AirDrop security page, it is probable that in AirDrop “Everyone mode” an attacker could find out the information of Apple devices around them:
For people using Apple devices or even other brands, especially in the US, take caution as this is a finding one Chinese local government published, who knows how many vectors of attack the US intelligence agencies is aware of.